n8n – CVE-2025-68613: Critical RCE Vulnerability


Threat actors have launched a new phishing campaign targeting Booking.com users, leveraging Unicode characters to disguise malicious links as legitimate ones. This attack shows how easily scammers can trick people with subtle visual deceptions.
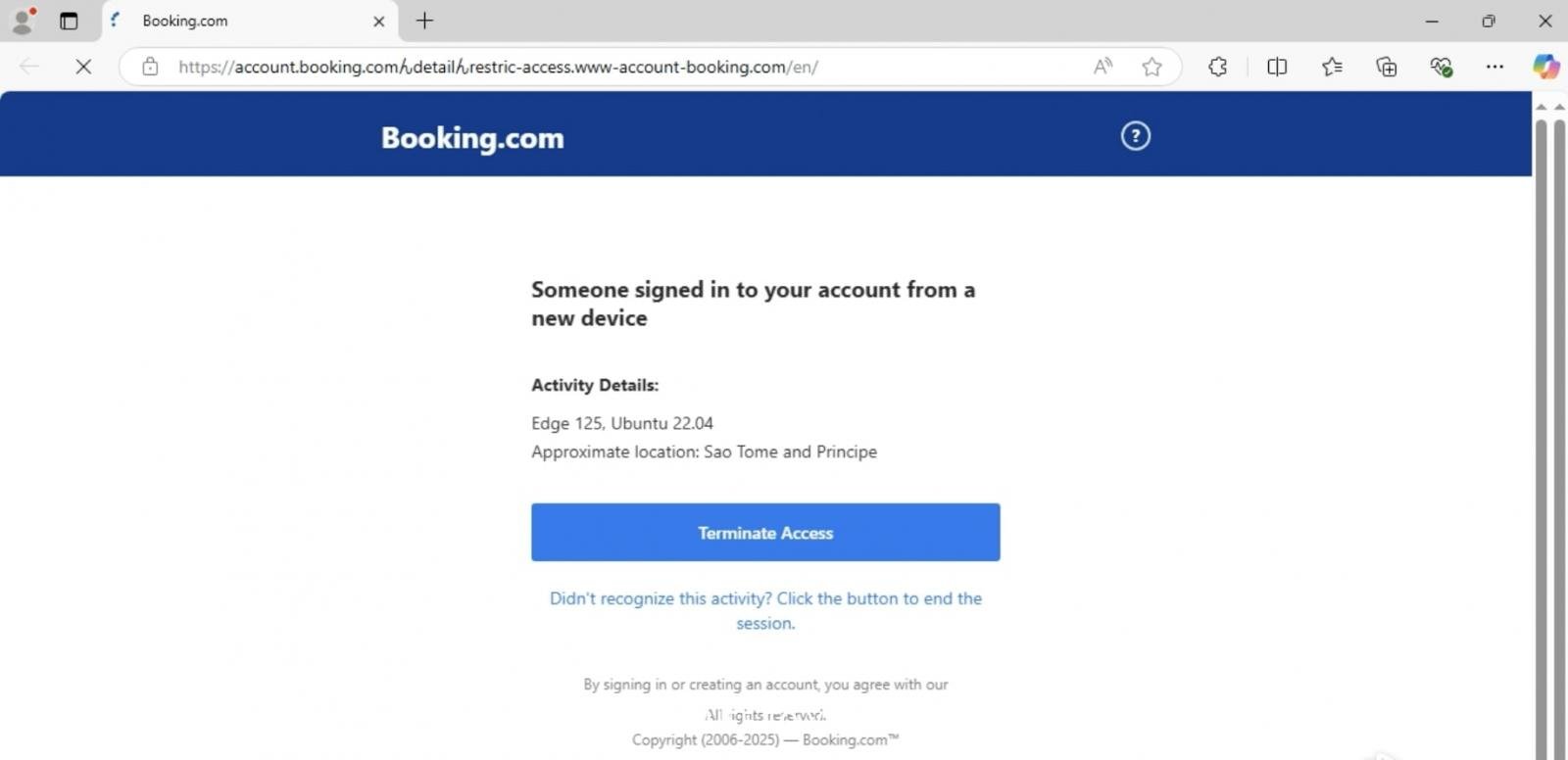
The campaign uses the Japanese hiragana character “ん” (Unicode U+3093) inside phishing URLs. On some systems and fonts, this symbol looks like a forward slash (/) or part of a subdirectory, making the fake URL appear genuine.
For example, a phishing email may display the link (appears safe but is deceptive):
https://admin.booking.com/hotel/hoteladmin/...But the actual malicious hyperlink is different (neutralized below for safety):
https://account.booking.comんdetailんrestric-access.www-account-booking[.]com/en/At first glance, it looks like a real Booking.com page. In reality, the true registered domain is “www-account-booking[.]com”, not booking.com. Everything before that is just a deceptive string.
Clicking the link leads victims to a malicious site that delivers a malicious MSI installer hosted on a CDN (neutralized for safety):
hxxps://updatessoftware.b-cdn[.]net/john/pr/04.08/IYTDTGTF.msiWhen executed, the installer can drop additional payloads such as information-stealing malware or remote access trojans (RATs), giving attackers access to the victim’s device.
Samples of this attack have been shared on MalwareBazaar and analyzed using any.run, confirming the infection chain.
This technique is part of homoglyph (or homograph) attacks, where characters from other alphabets look almost identical to Latin ones.
For example:
The use of “ん” is another example, exploiting typography and human error to trick users into trusting malicious links.
This isn’t the first time attackers have abused Booking.com:
The latest campaign proves that Booking.com remains a lucrative target for cybercriminals.
Here are key steps to defend against homoglyph phishing:
/.This Unicode-based phishing campaign highlights how attackers exploit tiny details to fool even careful users. As cybercriminals grow more inventive, vigilance is essential. A single deceptive character can turn a trusted site like Booking.com into a dangerous trap.
Comments
Post a Comment